Privacy vs. Security: How to Find the Balance in P2P Cryptocurrency Trading
The world of peer-to-peer (P2P) cryptocurrency trading is a complex and rapidly evolving landscape. As the popularity of cryptocurrencies like Bitcoin, Ethereum, and Monero continues to grow, concerns about user privacy have become increasingly important. In this article, we’ll take a closer look at the trade-offs between protecting users’ private data and ensuring their security in P2P cryptocurrency trading.
What are P2P cryptocurrency trading?
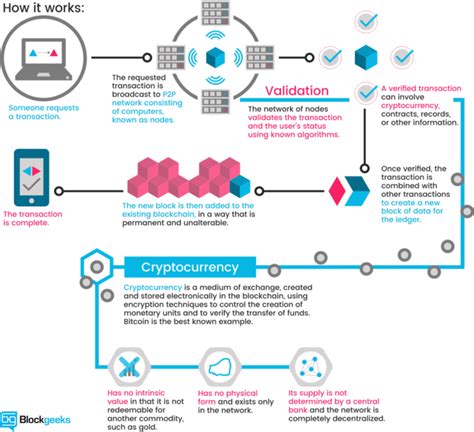
In a P2P cryptocurrency transaction, users send cryptocurrencies directly from one wallet to another, without going through a central authority such as an exchange or bank. This model allows for peer-to-peer trading and reduces the need for intermediaries, making it generally faster and cheaper than traditional exchange-based methods.
The Importance of User Privacy
User privacy is a key concern in P2P cryptocurrency transactions. When users send cryptocurrencies to other parties without using an intermediary, their private data can be exposed to third-party providers or hackers. This can lead to identity theft, phishing attacks, and other forms of cybercrime.
Security Considerations
Security is also paramount in P2P cryptocurrency transactions. Without the protection of intermediaries, it is easier for malicious actors to manipulate or steal cryptocurrencies. For example:
- Wallets: Users must store their private keys securely, which can be vulnerable to hacking if not properly protected.
- Network congestion: High network congestion can slow down transaction times and increase security risks.
- Intermediary Vulnerabilities: Weaknesses in intermediaries, such as exchanges or brokers, can create security vulnerabilities.
Balancing Privacy and Security
To strike a balance between protecting users’ private data and ensuring their security, P2P cryptocurrency transactions need to address both concerns. Here are some strategies:
- Use Secure Wallets: Users should use trusted wallet providers that offer strong security features, such as two-factor authentication (2FA), multi-signature wallets, or hardware wallets.
- Verify User Identity: Exchanges and brokers can verify user identities through KYC (Know Your Customer) and AML (Anti-Money Laundering) regulations to minimize the risk of identity theft.
- Implement network-specific security measures: P2P exchanges and brokers should implement network-specific security measures, such as end-to-end encryption, secure communication protocols, or anti-phishing technologies.
- Monitor transactions: Users should regularly monitor their transactions for any suspicious activity or potential security breaches.
Conclusion
Protecting users’ private data while ensuring their security in P2P crypto transactions requires a delicate balance between the two concerns. By using secure wallets, verifying user identity, implementing network-specific security measures, and monitoring transactions, P2P exchanges and brokers can minimize the risks associated with these transactions. As the cryptocurrency landscape continues to evolve, it is essential that users stay informed about the latest security best practices and take steps to protect their private data.
Additional Resources
- Cryptocurrency Security Guides
: [1]( [2](
- Peer-to-peer cryptocurrency trading platforms
: [3]( [4](

